End of the Road is a capstone challenge from DEADFACE CTF 2023. This challenge emphasizes the need to treat the CTF like one large story and investigation by aggregating information found on DEADFACE in various other challenges. Throughout many of the challenges are data and artifacts left behind by DEADFACE that need to be used to solve this challenge: things such as passwords, keys, and files.
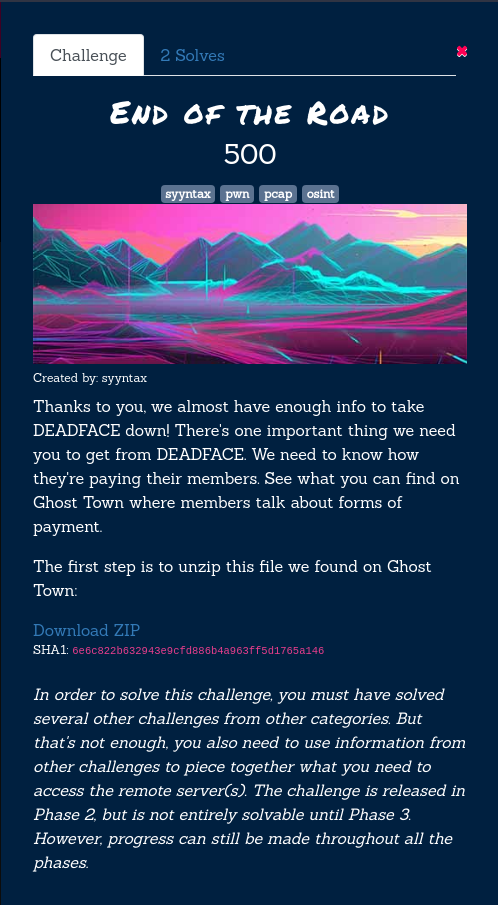
Challenge Description
In the End of the Road, players need to aggregate their findings from previous challenges to access DEADFACE's sensitive data, decrypt the instructions, solicit a request from their processing host, and ultimately find the flag associated with a cryptocurrency wallet that DEADFACE owns.
Step 1: Find the Ghost Town thread
First, players need to find the relevant Ghost Town thread. Players can find this thread by searching for file.deadface.io or just perusing the site to figure out how DEADFACE members would get paid for their efforts.
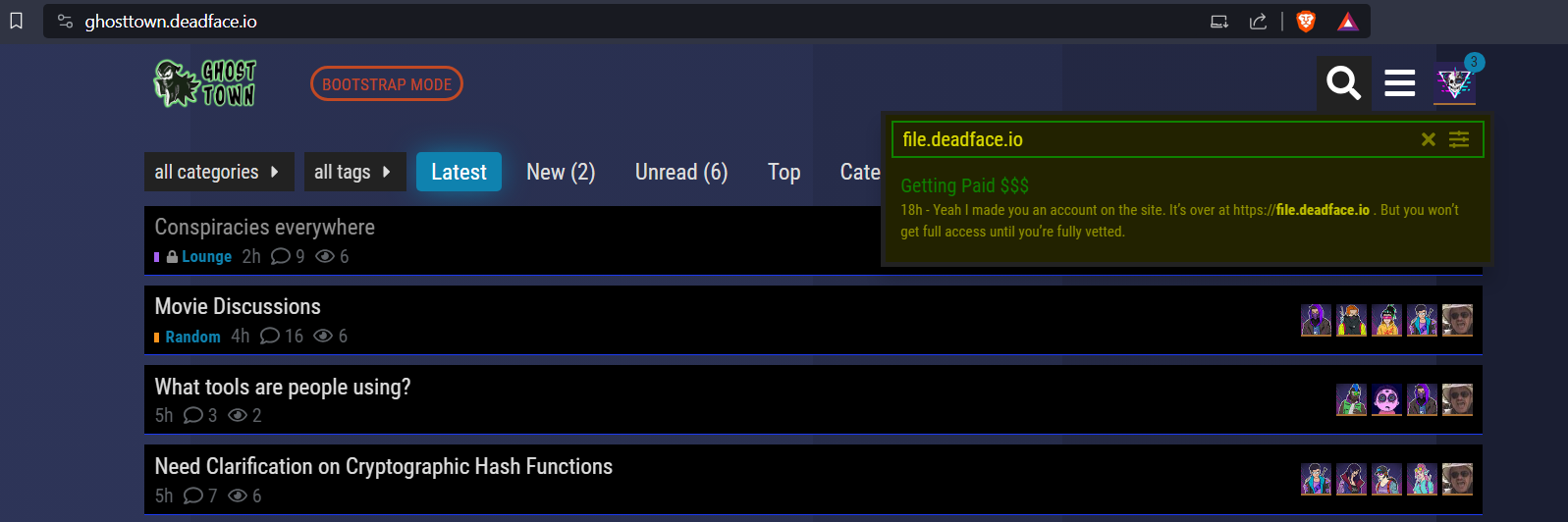
Note: the challenge was changed mid-competition due to a failure of the file.deadface.io site. Originally, players were meant to find the site, login to it, then grab the necessary files. Due to the site failing, the files were provided in an encrypted zip file with gh0st404's password.
The thread shows spookyboi explaining the process for getting paid. gh0st404 asks for the site address; spookyboi responds telling him he created an account for him. At the bottom of the thread, gh0st404 mentions he just zipped the files and encrypted them.
Step 2: Decrypt the Zip file
Because gh0st404 mentioned that he zipped them, players can assume the zip file is encrypted with one of his passwords. Players must have solved Host Busters 5 to know gh0st404's password (it was the flag from that challenge).
Once unzipped, 2 important files can be found: instructions.link.encrypted and notes.md. The instructions.link.encryptedfile is encrypted with spookyboi’s public key. We know this based on his original post in the aforementioned Ghost Town thread. Reading the notes.md file, players will get more information:
# Notes
`instructions.link.encrypted` contains instructions for sending data over to the processing site.
The file `instructions.link.encrypted` is encrypted with my public key. We had issues last year with these instructions finding their way to unauthorized people. If you don't have these instructions, it's because you're not vetted yet. Only my private key will unlock this file. The processing site has my private key and will unlock data you send to it.
Any questions, talk to me, `mort1cia`, or `d34th`.Step 3: Decrypt the Instructions
This is, again, where solving a previous challenge comes into play. In Host Busters 4, players can use the method used to solve that challenge to read and copy spookyboi’s private and public keys in his .keys directory.
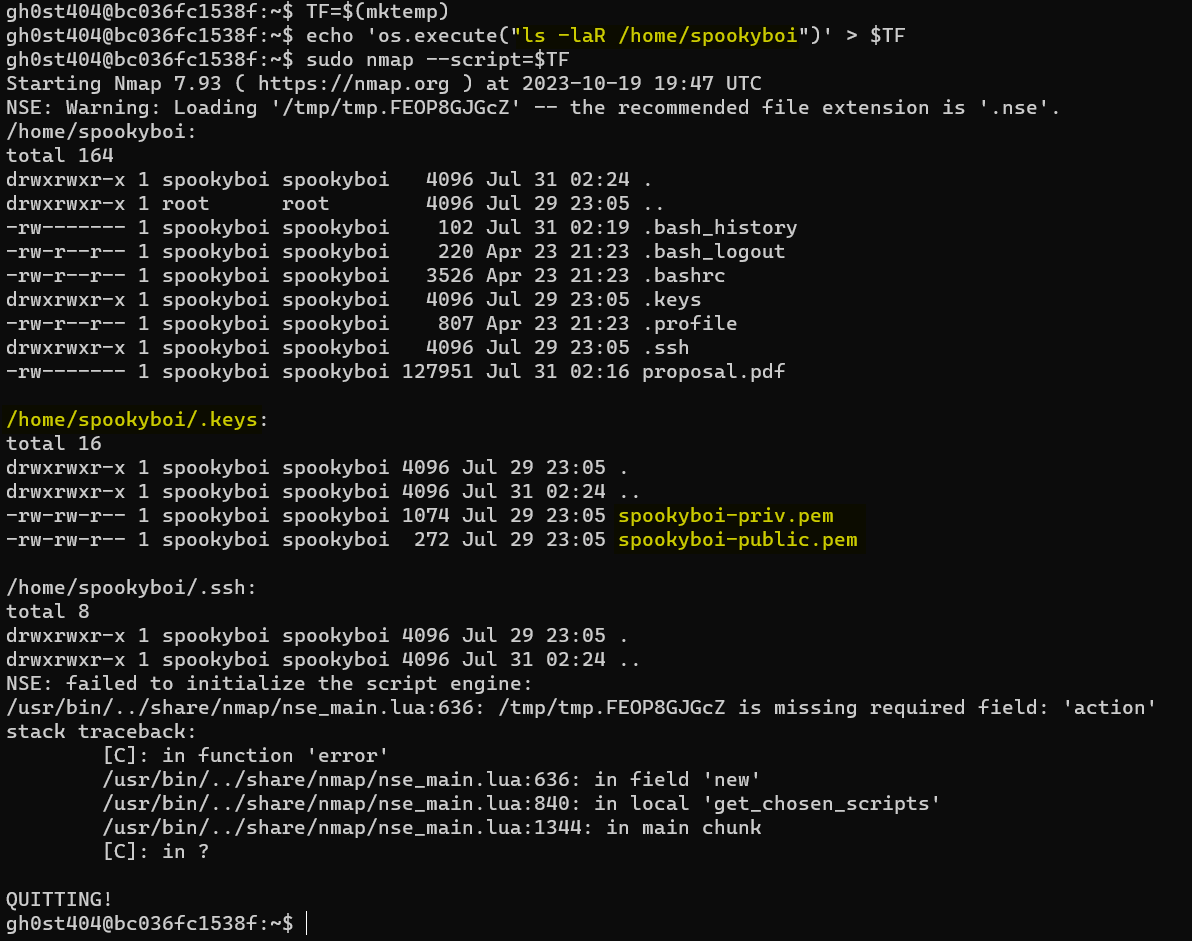
Players can cat these two files and save them on their own systems for use in this challenge.
Here’s where another piece of information from another challenge is required. Players will need spookyboi’s password from the Git Rekt traffic analysis challenge. His password is the flag for that challenge: SpectralSecrets#2023.
After players have the keys and password, they can use spookyboi’s private key to decrypt the instructions.link.encrypted file. The result will be a link to the instructions: https://tinyurl.com/3ez9x89e.
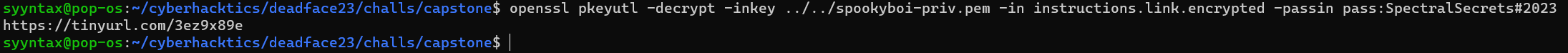
openssl pkeyutl -decrypt -inkey spookyboi-priv.pem -in instructions.link.encrypted -passin pass:SpectralSecrets#2023Step 4: Read the Instructions
Next, players can access the link to read the instructions:
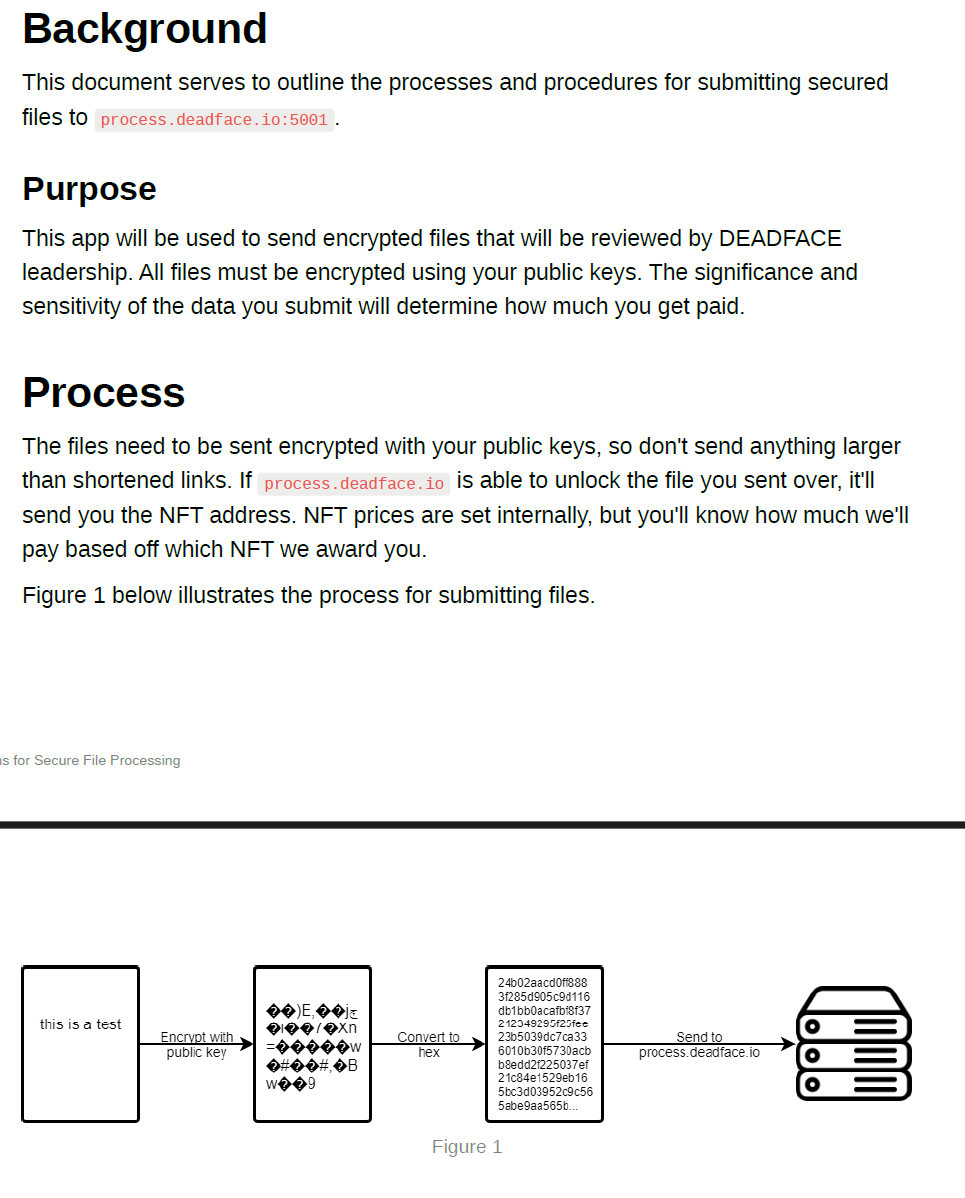
The PDF from the link tells players to create a file, encrypt it with their public key (in this case, spookyboi's public key), convert the file to hex, and send it to process.deadface.io.
Step 5: Send data to process.deadface.io
Using the instructions in the PDF, players can use the following command to encrypt any data with spookyboi’s puiblic key and send it to the processing system.
touch file.txt
openssl pkeyutl -encrypt -inkey spookyboi-public.pem -pubin -in file.txt -out file.encrypted
xxd -p -c256 file.encrypted | nc process.deadface.io 5001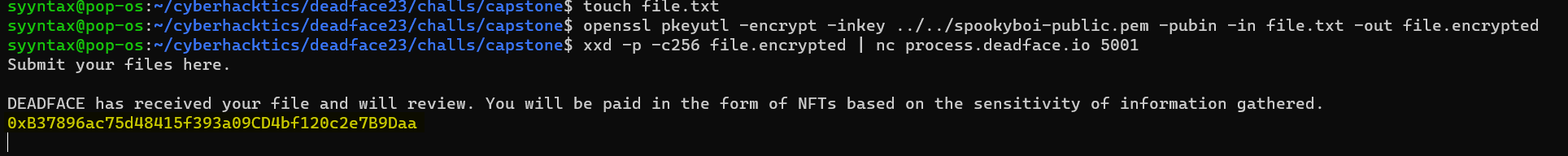
Step 6: Find the NFT
The response gives a wallet address of 0xB37896ac75d48415f393a09CD4bf120c2e7B9Daa. Go to https://opensea.io, a popular NFT site that lets you generate your own NFTs, and search for this wallet address.
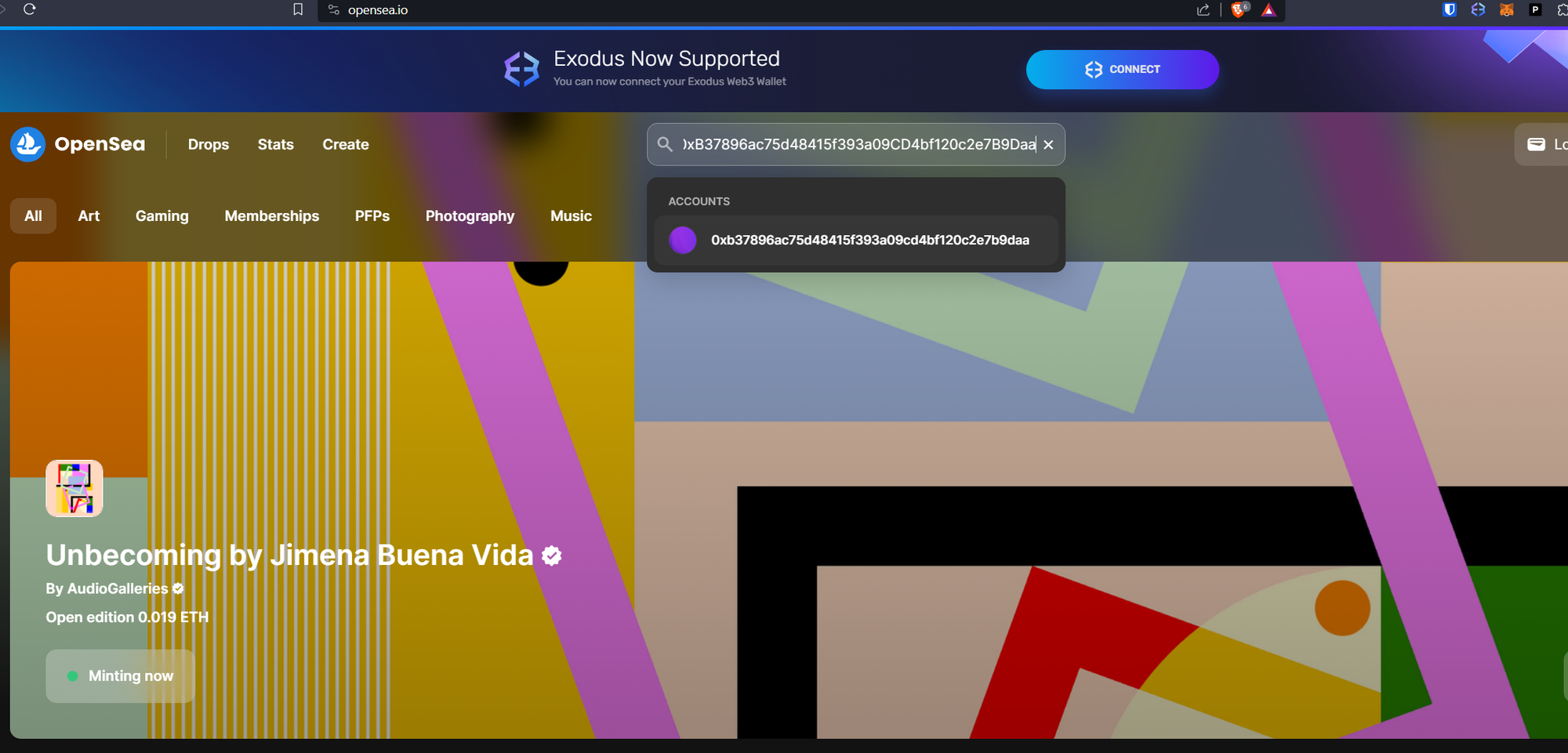
Players will see an NFT associated with the wallet.
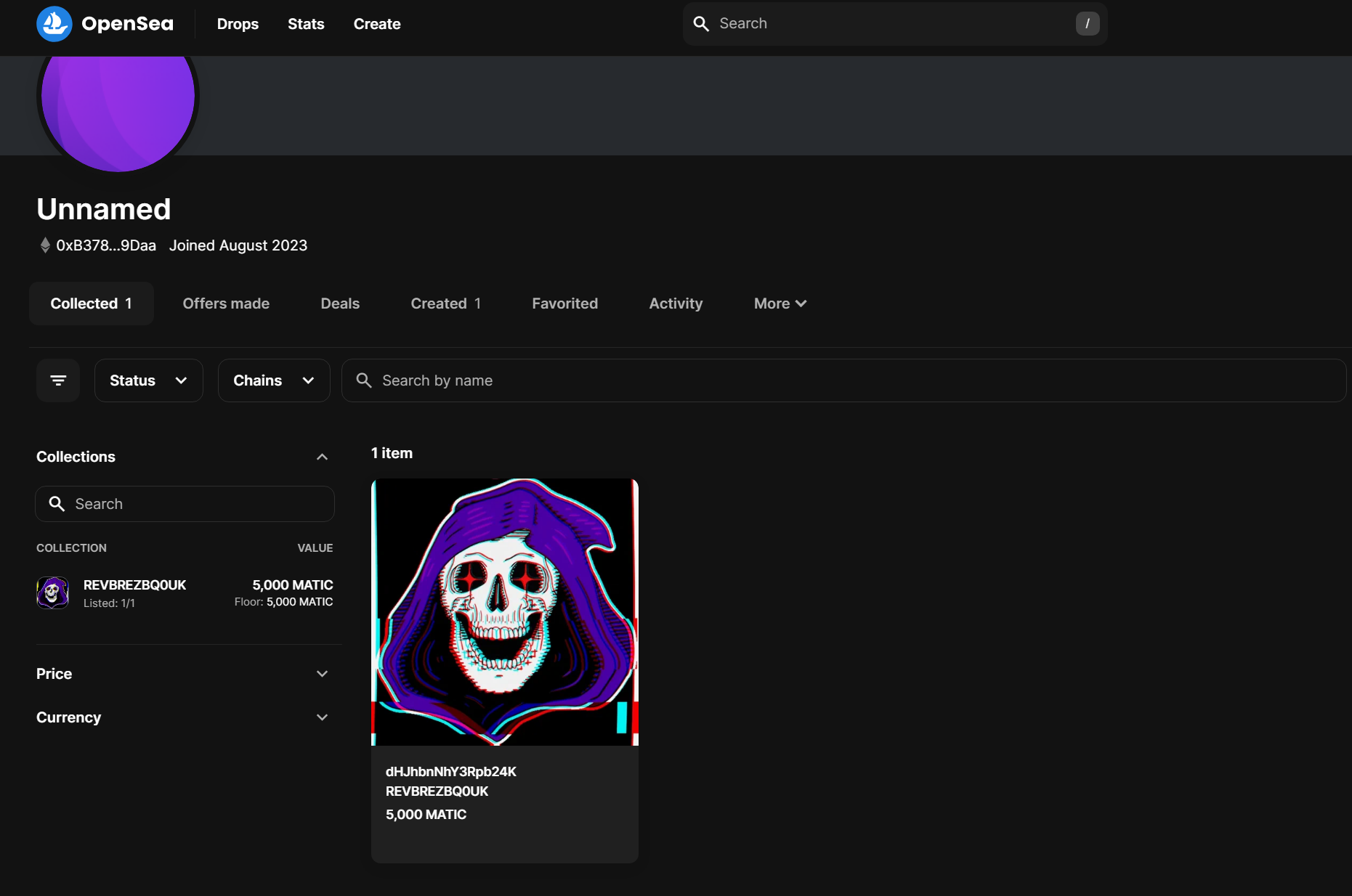
If players click on the NFT, they will see the flag in the Description field of the NFT.
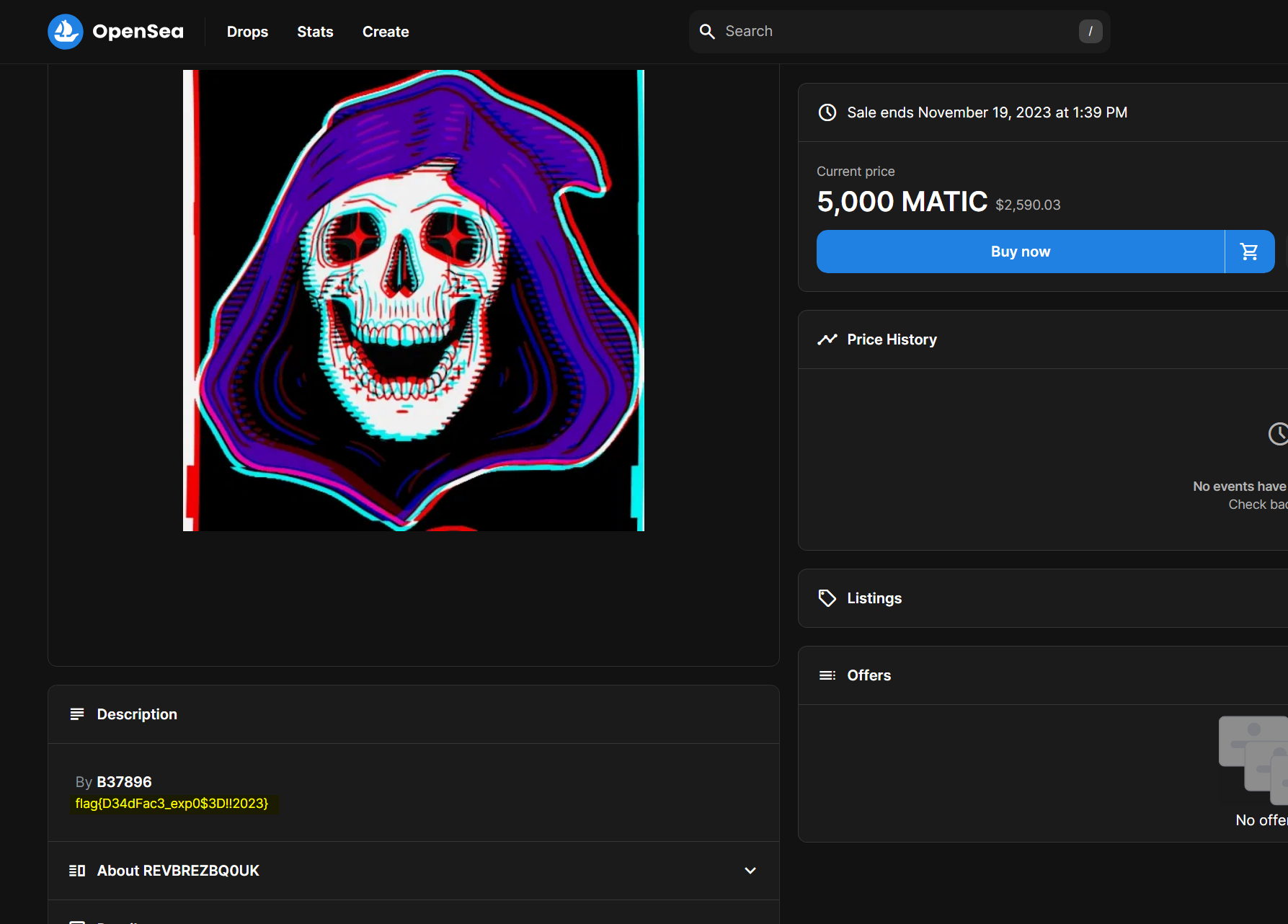
And there we have it, the flag is: flag{D34dFac3_exp0$3D!!2023}
Conclusion
The goal of this challenge was to emphasize the importance of collection data during an engagement or campaign and using it to follow the story of DEADFACE. The challenge required knowledge in various categories rather than being a standalone challenge.


