Sneaky Static is a steganography challenge from DEADFACE CTF 2023. This challenge requires players to find an mp4file appended to another mp4. Common steganography tools will not be able to detect or carve out the hidden file.
Challenge Description
In the Sneaky Static challenge, players are given a video that contains two separate mp4 files and must figure out how to extract the hidden file.
Players can download the video from the link in the challenge. When players play the video, it will show a 2-second clip:

If players use exiftool, they’ll get their first indication that a second video is hidden in video.mp4.
exiftool video.mp4Looking at the metadata, players will see an “Ingredients File Path” showing video2.mp4.
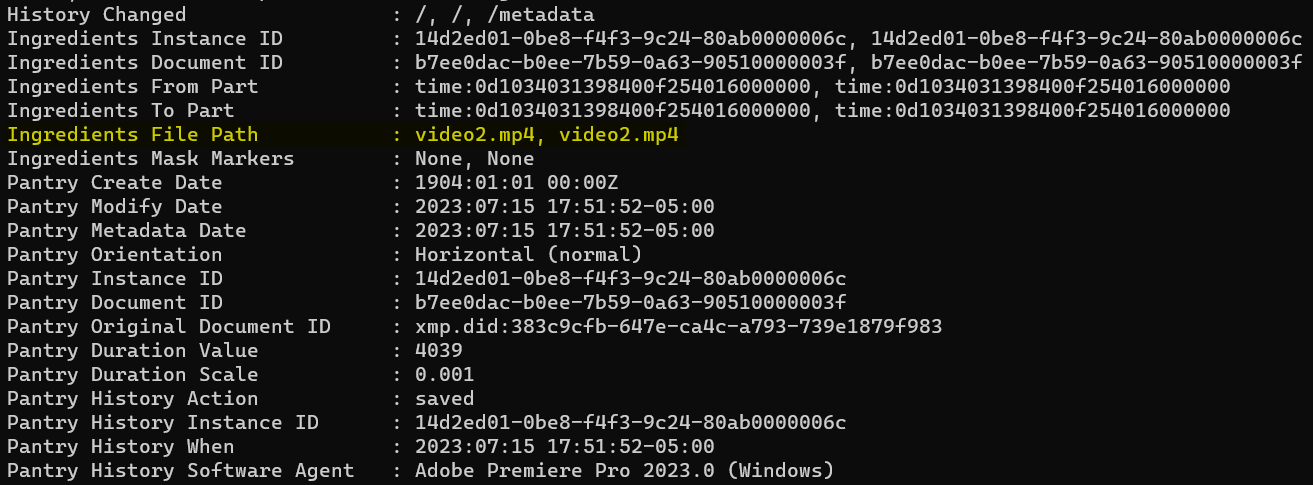
MP4 videos start with an ftyp atom - a type of structure in an MP4 file. An ftyp atom defines the file type and the common data structures used (https://openmp4file.com/format.html). Players can perform a string search using hexeditor for ftyp. They’ll see there are two ftyp atoms: one at 0x00000000 and another at 0x001A73F7.
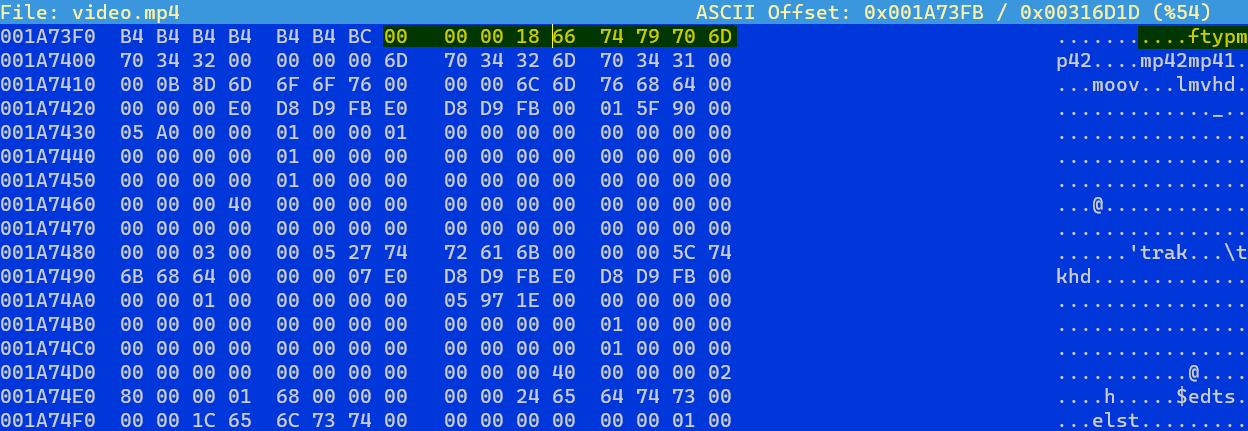
The hexadecimal offset value (0x001A73F7) can be converted to decimal (1733623) here: https://www.rapidtables.com/convert/number/hex-to-decimal.html
The following dd command can be used to carve out the second video:
dd if=video.mp4 of=video_new.mp4 bs=1 skip=1733623Once players open the new video (e.g., video_new.mp4), they’ll see the flag in the extracted video.

Conclusion
One of the goals with this challenge was to encourage players to get away from common tools and understand mp4 file structures. Sometimes, utilizing common tools can be crutch and may not always work in real-world situations. It's important to understand how files are stuctured, and thus how they can be altered for other purposes.


