This is another steganography challenge that required the use of several tools atypical of traditional steganography. I found this one very challenging at first, and it required a lot of research on my part, but I really enjoyed it!
Accessing the Challenge
Clicking on the challenge revealed the following message that guides you towards solving the challenge.
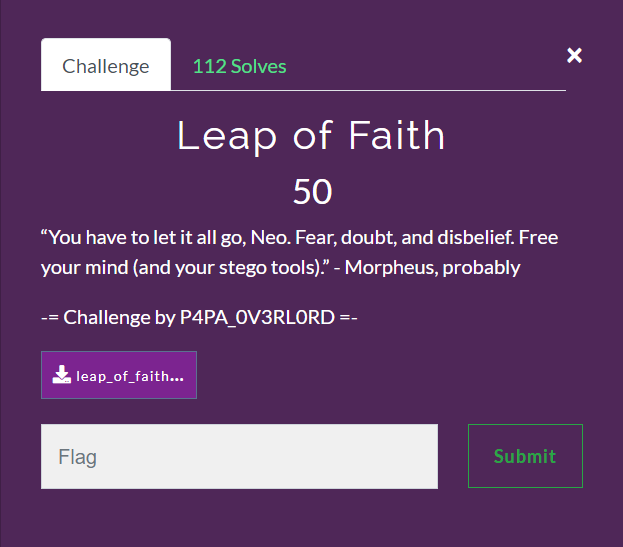
There isn't much information provided for this challenge, except for a quote from The Matrix and a nice little hint regarding "stego tools".
The attachment in the challenge provided the image seen below.

Searching for Hidden Data
As I do for all steganography challenges, I attempted to find hidden information in the image using exiftool and strings. In this case, neither of those tools revealed any hidden information.
The next step in my steganography methodology was to use binwalk to find additional files hidden within the image.
binwalk leap_of_faith.jpeg
Binwalk revealed another JPEG image hidden in the original.
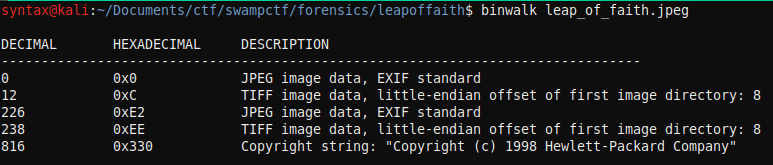
Normally, I would use binwalk with the -e option to extract the additional files in the image; however, in this case, binwalk was unable to extract the files. So, I headed off to Google.
Using DD to Extract the Hidden Files
My search results led me to a github page for CTF write-ups for other CTFs (https://github.com/VulnHub/ctf-writeups/blob/master/2016/sctf/banana-boy.md). Using this individual's write-up as a reference, I used dd to extract the hidden image.
Looking at the binwalk output, we can see that the second image offset occurs at 226, so that's where I skipped to in my dd command. I defaulted to using bs=1, which reads 1 byte at a time.
dd if=leap_of_faith.jpeg of=out.jpeg skip=226 bs=1
Upon executing dd, the following image was extracted.

This is where I got stuck for a little bit. I tried my typical steganography methods on this new image by using exiftool, strings, and a variety of other tools, but I couldn't find any additional information hidden in this image.
After playing around with the dd command and various options, I finally decided to change the bs option to 2 just to give it a shot. Fortunately for me, it resulted in the following image being extracted.
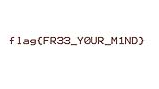
Conclusion
While I ended up finding the flag, I'm still not satisfied that I don't fully understand how this challenge was built or how the creator hid this image. The challenge itself was great! It's unlike any other steganography challenge I've seen before, and I really enjoyed figuring this one out.


