Technology photo created by freepik - www.freepik.com
Phishing attacks are a common type of cybercrime that hackers and scammers perform to compromise credentials, personal data, or other sensitive information (like medical data). It's easy to be fooled by phishing attacks if you don't know how to detect the signs that you're being phished. In this blog, I'll dissect a real-world phishing email that was sent to me personally and highlight all of the warning signs in the email.
What is a Phishing Scam?
But first, what exactly is a phishing scam?
Phishing scams are attempts by scammers to trick you into giving out personal information such as your bank account numbers, passwords, credit card numbers, or other sensitive data. This is usually done through the use of deceptive websites or email.
According to the FBI's 2020 Internet Crime Report, phishing (and its variants) claimed 241,342 victims and were the most successful cyber attacks in 2020.
How Phishing Scams Work
Phishing scams use emails made to look legitimate. Common examples include emails made to look like bogus monetary transactions or emails that look as though you conveniently won a prize of some sort. More sophisticated, targeted phishing scams will look as though they are coming from within your organization (e.g. an email from your "boss" telling you to sign in on some website for compliance reasons).
One thing that these phishing scams have in common is that they try to sound urgent. After all, if they sound urgent, they may get their victims to rush to action, thus missing common indicators of the scam.
Real-World Example
The other day, I was sent a phishing email from "Wells Fargo" informing me that my bank account was being limited due to a login from an unrecognized device.
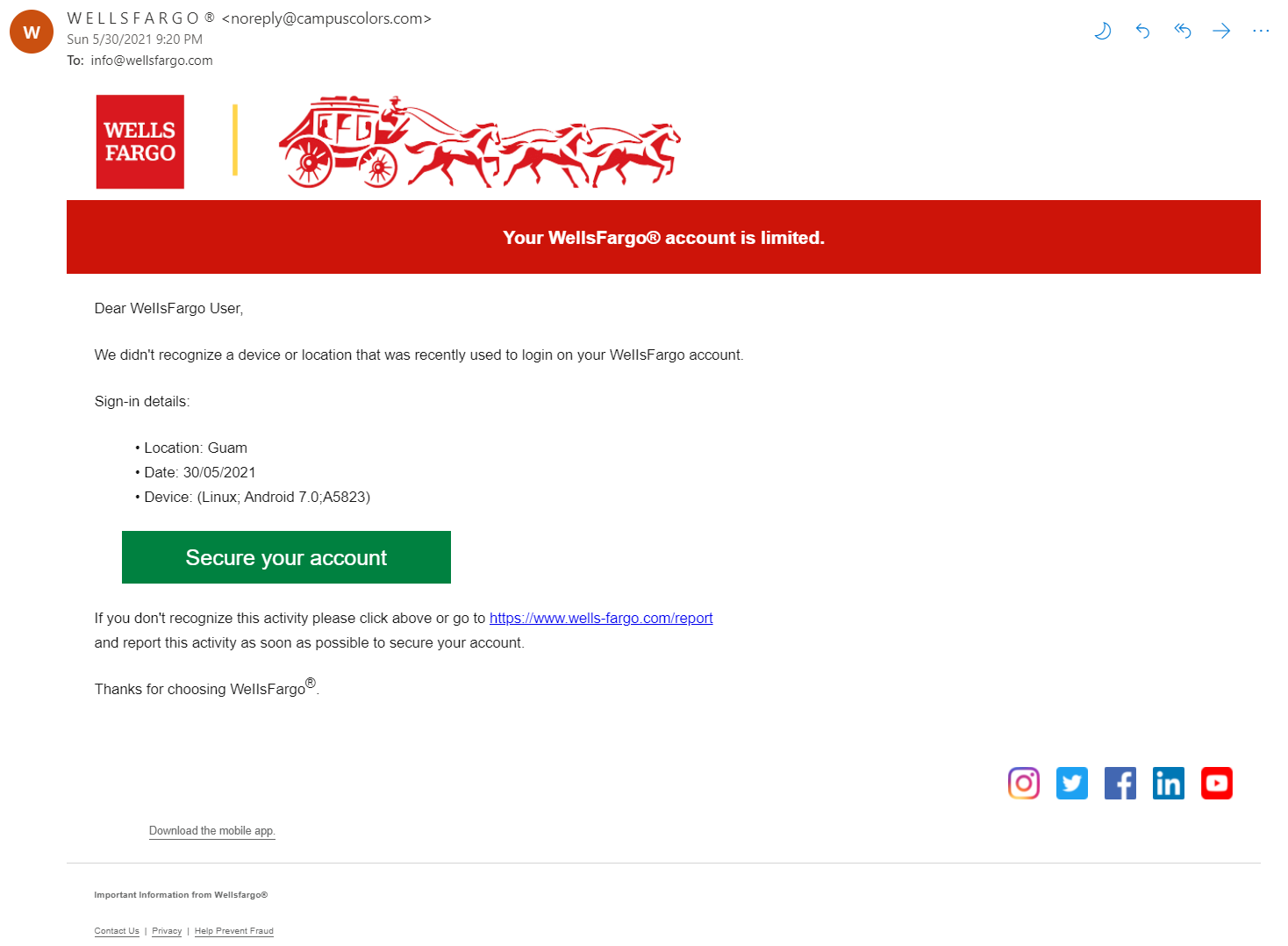
This is where the scammers try to induce a sense of urgency. A victim's knee-jerk reaction may be to click the giant Secure your account button to make sure whoever is accessing the account from Guam doesn't withdraw any funds. But before we panic, let's inspect the email and see what kinds of indicators exist that would tell us if this email is legitimate or not.
Red Flag #1: The Sender
The first giveaway that this email was illegitimate was the sender of the email. First, the sender name was "W E L L S F A R G O (R)", all caps, spaces between letters. That seemed a little odd. But, maybe it's legitimate, so let's move on.
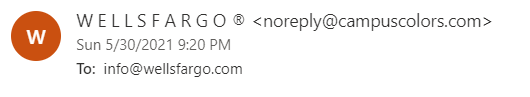
The sender of the email was noreply@campuscolors.com. That's definitely strange. Why is Wells Fargo sending me an email from Campus Colors? What is Campus Colors? Right away, we already have enough information to determine that this is a phishing email. But let's go ahead and look at what other indicators we have.
Campus Colors
I was curious if Campus Colors was a legitimate website, since I had never heard of it before. I did some quick Googling and found that it is, in fact, a real legitimate site. I'm not sure why the scammers chose to come from that website.
Red Flag #2: The Recipient
If we look at the "To" section, the email is addresses to info@wellsfargo.com. Maybe the scammers were expecting the victim to see the "To" and mistake it as the sender?
Red Flag #3: The Greeting
Most companies will refer to their clients' names in the email. This isn't always the case, but any time a reputable company refers to me as "User" or "Customer", it sends off a red flag.
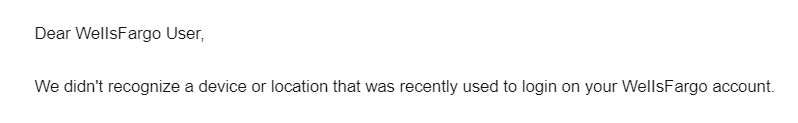
I also thought it was odd that they concatenated WellsFargo into one word. Nowhere on the official website for Wells Fargo do they concatenate their business name like that.
Red Flag #4: The Hyperlink
If you ever feel compelled to click hyperlinks in emails, you should at least hover over the link beforehand and see where it's taking you. I hovered over both hyperlinks in the email: the big green button and the hyperlink in the sentence beneath it. Both hyperlinks go somewhere other than a Wells Fargo site.
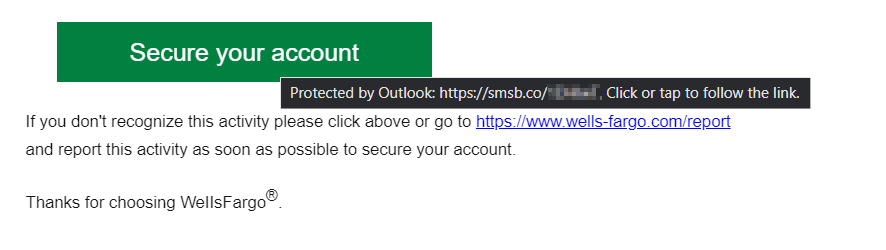
As you can see in the email above, the link would have taken me to smsb.co, which is a URL shortener for Text Marketing Platforms (I obfuscated the link for readers' safety). Doesn't sound like Wells Fargo.
Another thing I noticed was the hyperlink looked as though it would take you to Wells Fargo, but their official URL does not contain a hyphen between "Wells" and "Fargo".
Red Flag #5: Business Name Capitalization
At the bottom of the email, the sender forgot to capitalize the "F" is "Wellsfargo". A common trait seen in phishing emails is their inconsistent use of capitalization, grammar, or spelling.

Red Flag #6: Inconsistent Links
At the bottom of the email were links to various social media platforms (i.e. Instagram, Twitter, Facebook, etc.) When I clicked the links (from a secure VM), they all took me to the official, respective social media pages for Capital One. It's pretty funny to see a Wells Fargo email linking to Capital One social media pages. It's likely the scammers use a base template and were too lazy to change all the context to Wells Fargo.
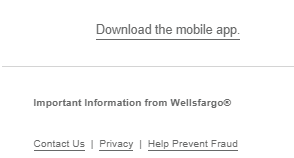
Red Flag #7: Nonfunctioning Links
At the bottom of the email were underlined text that I assumed were links. One of the lines said Download the mobile app.. I hovered over it and no link appeared. I clicked it and it didn't take me anywhere. The same was true for the Contact Us, Privacy, and Help Prevent Fraud lines.
Red Flags
Here's a list of all the red flags I found, some of which I talked about and some I didn't bring up:
- Sender name is all caps and spaced out
- Sender email address is not from Wells Fargo, but from Campus Colors
- Recipient email address is info@wellsfargo.com, rather than my email
- Email addresses me as "WellsFargo User", rather than my actual name
- The email consistently concatenates Wells Fargo as "WellsFargo", something the official Wells Fargo website doesn't do
- The hyperlinks for the
Secure your accountbutton and the link to Wells Fargo actually goes to an smsb.co link, a URL shortener. - Bad grammar (e.g. "If you don't recognize this activity please click above..." should have a comma after "activity"
- The social media icons at the bottom of the email go to pages affiliated with Capital One
- The "f" in "Wellsfargo" at the bottom of the email is lowercase
- None of the links below the social media icons work
Analysis
After reading and inspecting the email, I had more than enough information to determine that the email was a phishing scam. I decided to then do some further analysis to see if I could find out where the email was coming from.
Who Sent the Email?
I went to my inbox and checked the source details of the email. Looking at the output, I was able to determine that the sender's IP address was 54.240.9.67, an IP affiliated with Amazon's Simple Email Service (SES). Amazon SES is a paid service that allows customers to configure email senders for marketing or other purposes.
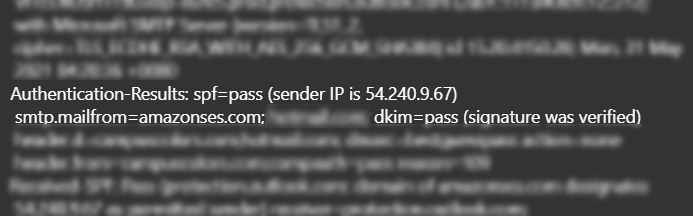
I'm fairly certain that Wells Fargo wouldn't be using Amazon SES to send emails to their clients. Using paid services likes Amazon SES is a method scammers use for non-attribution.
Conclusion
Phishing scams are one of the most effective scams out there for compromising credentials, personal data, and other sensitive information. Knowing the signs and taking the time to inspect emails are all part of good cybersecurity hygiene.


